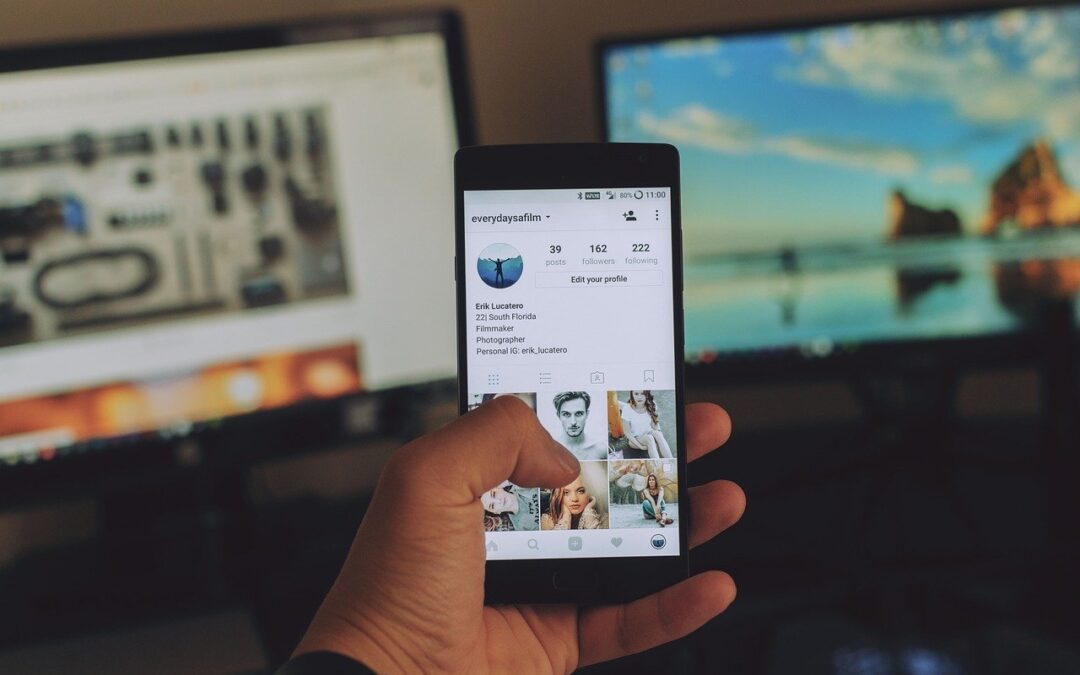
Jul 11, 2022 | Information Technology Law, Intellectual Property
Social Media is Unavoidable. We’re confronted with social media in its various forms everyday. Politicians are endlessly tweeting and the person next to you on the bus is scrolling through... Read More

Jul 2, 2022 | Information Technology Law, Intellectual Property
Are you a mobile app developer or someone contracting with a developer to make mobile apps? This article aims to set out briefly some of the common copyright disputes that... Read More

May 21, 2022 | Information Technology Law
The Office of the Australian Information Commissioner has found that Uber failed to protect the personal data of Australians following a cyber-attack in 2016. Uber had been able to prevent... Read More

Apr 2, 2022 | Employment Law, Information Technology Law
Workplace surveillance and email monitoring have become the norm in organisations across Australia. However, many employees still do not understand their obligations or their rights when it comes to the... Read More

Mar 17, 2022 | Information Technology Law
The internet remains one of the most indispensable marketing tools for businesses, and a domain name is a piece of valuable intellectual property. However, domains are susceptible to being altered... Read More

Feb 4, 2022 | Information Technology Law
The digital landscape of cryptocurrency has drastically evolved with the emergence of NFTs. In 2021, businessman Sina Estavi purchased Twitter founder Jack Dorsey’s first-ever tweet for over $2.8m. Despite this... Read More







